二进制包搭建k8s集群
环境信息:
|c720111.xiodi.cn |192.168.20.111 |k8s master-1 |
|c720112.xiodi.cn |192.168.20.112 |k8s master-2 |
|c720113.xiodi.cn |192.168.20.113 |k8s master-3 |
|c720114.xiodi.cn |192.168.20.114 |k8s slave-1 |
|c720115.xiodi.cn |192.168.20.115 |k8s slave-2 |
|c720116.xiodi.cn |192.168.20.116 |k8s master vip|
部署过程:
1. 系统升级
由于k8s在较低内核中存在某些bug,因此需要先升级下内核。建议使用4.10或以上版本。
1.1 下载地址
软件包百度网盘:
https://pan.baidu.com/s/1JtecfQoZISxN2EQRVrjKdg 6taj
1.2 执行以下命令进行内核升级
# 升级内核 $ wget https://elrepo.org/linux/kernel/el7/x86_64/RPMS/kernel-ml-5.0.4-1.el7.elrepo.x86_64.rpm $ wget https://elrepo.org/linux/kernel/el7/x86_64/RPMS/kernel-ml-devel-5.0.4-1.el7.elrepo.x86_64.rpm $ yum -y install kernel-ml-5.0.4-1.el7.elrepo.x86_64.rpm kernel-ml-devel-5.0.4-1.el7.elrepo.x86_64.rpm # 调整默认内核启动 $ cat /boot/grub2/grub.cfg |grep menuentry $ grub2-set-default "CentOS Linux (5.0.4-1.el7.elrepo.x86_64) 7 (Core)" # 检查是否修改正确 $ grub2-editenv list $ reboot
1.3 IPVS的支持开启
# 确认内核版本后,开启 IPVS
$ uname -a
$ cat > /etc/sysconfig/modules/ipvs.modules <<EOF
#!/bin/bash
ipvs_modules="ip_vs ip_vs_lc ip_vs_wlc ip_vs_rr ip_vs_wrr ip_vs_lblc ip_vs_lblcr ip_vs_dh ip_vs_sh ip_vs_fo ip_vs_nq ip_vs_sed ip_vs_ftp nf_conntrack"
for kernel_module in \${ipvs_modules}; do
/sbin/modinfo -F filename \${kernel_module} > /dev/null 2>&1
if [ $? -eq 0 ]; then
/sbin/modprobe \${kernel_module}
fi
done
EOF
$ chmod 755 /etc/sysconfig/modules/ipvs.modules && bash /etc/sysconfig/modules/ipvs.modules && lsmod | grep ip_vs
1.4 关闭交换分区,Selinux及Firewalld等
# 关闭 Selinux/firewalld
$ systemctl stop firewalld && systemctl disable firewalld
$ setenforce 0
$ sed -i "s/SELINUX=enforcing/SELINUX=disabled/g" /etc/selinux/config
# 关闭交换分区
$ swapoff -a
$ cp /etc/{fstab,fstab.bak}
$ cat /etc/fstab.bak | grep -v swap > /etc/fstab
# 设置 iptables
$ echo """
vm.swappiness = 0
net.bridge.bridge-nf-call-iptables = 1
net.ipv4.ip_forward = 1
net.bridge.bridge-nf-call-ip6tables = 1
""" > /etc/sysctl.conf
$ sysctl -p
1.5 配置主机名的解析及时间的同步(略)
1.6 配置各个主机能够免密钥进行通信
# 此处配置c720111.xiodi.cn能够和其它几个主机免密钥互通 [root@c720111 ~]# ssh-keygen [root@c720111 ~]# ssh-copy-id root@192.168.20.111 [root@c720111 ~]# ssh-copy-id root@192.168.20.112 [root@c720111 ~]# ssh-copy-id root@192.168.20.113 [root@c720111 ~]# ssh-copy-id root@192.168.20.114 [root@c720111 ~]# ssh-copy-id root@192.168.20.115
2. 签发证书
2.1 证书签发配置
wget https://pkg.cfssl.org/R1.2/cfssl_linux-amd64 wget https://pkg.cfssl.org/R1.2/cfssljson_linux-amd64 wget https://pkg.cfssl.org/R1.2/cfssl-certinfo_linux-amd64
chmod +x cfssl cfssljson mv cfssl cfssljson /usr/local/bin/
将会分别为下列组件签发证书:
- admin user
- kubelet
- kube-controller-manager
- kube-proxy
- kube-scheduler
- kube-api
2.2 创建CA证书配置请求
(1)产生ca证书
CA证书配置请求
$ cat > ca-config.json <<EOF
{
"signing": {
"default": {
"expiry": "8760h"
},
"profiles": {
"kubernetes": {
"usages": ["signing", "key encipherment", "server auth", "client auth"],
"expiry": "8760h"
}
}
}
}
EOF
CA证书签名请求
$ cat > ca-csr.json <<EOF
{
"CN": "Kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"L": "Shanghai",
"O": "xiodi",
"OU": "CA",
"ST": "Winterfell"
}
]
}
EOF
产生CA证书
$ cfssl gencert -initca ca-csr.json | cfssljson -bare ca # 查看产生的证书 [root@c720111 tmp]# ls -al -rw------- 1 root root 1675 Mar 23 11:04 ca-key.pem -rw-r--r-- 1 root root 1314 Mar 23 11:04 ca.pem
(2)产生admin用户证书
证书签名请求配置:
$ cat > admin-csr.json <<EOF
{
"CN": "admin",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "system:masters",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
产生admin用户证书并校验结果:
# 产生证书 $ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes admin-csr.json | cfssljson -bare admin # 查看产生的证书 [root@c720111 tmp]# ls admin-key.pem admin.pem
3. kubelet Client端证书
3.1 节点授权 节点的授权是一种特殊用途的授权模式,由kubelets API请求明确授权。
节点的授权允许kubelet去执行API操作,包括: - 读操作 - services - endpoints - nodes - pods secret,configmaps,persistent volume claims 和persistent volues相关缩写的pod - 写操作 - 节点和节点的状态(使NodeRestriction准入插件限制kubelet修改自己的节点) - pods和po的状态(使NodeRestriction准入插件限制kubelet修改绑定到本身的Pods) - 事件 - 认证相关的操作 - 读/写访问certificationsigningrequests TLS引导的API - 能够创建tokenreviews和subjectaccessreviews委托认证/授权检查 为了能够通过节点授权,kubeletes必须使用一个凭证来标识它们是`system:nodes`组,是带有`systema:node:<nodeName>`名称 。 具体详情参考:https://kubernetes.io/docs/reference/access-authn-authz/node/
3.2 执行如下命令产生关于kubelet的证书
# 配置worker节点相关信息
$ cat workers.txt
c720114.xiodi.cn 192.168.20.114
c720115.xiodi.cn 192.168.20.115
# 创建脚本文件,内容如下
$ cat generate-kubelet-certificate.sh
IFS=$‘\n‘
for line in `cat workers.txt`; do
instance=`echo $line | awk ‘{print $1}‘`
INTERNAL_IP=`echo $line | awk ‘{print $2}‘`
cat > ${instance}-csr.json <<EOF
{
"CN": "system:node:${instance}",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "system:nodes",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -hostname=${instance},${INTERNAL_IP} -profile=kubernetes ${instance}-csr.json | cfssljson -bare ${instance}
done
# 产生证书并进行查看
$ sh generate-kubelet-certificate.sh
$ ls -l
-rw------- 1 root root 1679 Mar 23 11:28 c720114.xiodi.cn-key.pem
-rw-r--r-- 1 root root 1521 Mar 23 11:28 c720114.xiodi.cn.pem
-rw------- 1 root root 1679 Mar 23 11:28 c720115.xiodi.cn-key.pem
-rw-r--r-- 1 root root 1521 Mar 23 11:28 c720115.xiodi.cn.pem
4. Controller Manager客户端证书
1. kube-controller-manager证书签名请求内容如下:
$ cat > kube-controller-manager-csr.json <<EOF
{
"CN": "system:kube-controller-manager",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "system:kube-controller-manager",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
2. 针对kube-controller-manager进行签发证书
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-controller-manager-csr.json | cfssljson -bare kube-controller-manager
# 校验产生的证书
$ ls kube-controller-manager*
kube-controller-manager.csr kube-controller-manager-key.pem
kube-controller-manager-csr.json kube-controller-manager.pem
5. Kube Proxy客户端证书
5.1 kube-proxy证书签名请求配置
$ cat > kube-proxy-csr.json <<EOF
{
"CN": "system:kube-proxy",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "system:node-proxier",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
5.2 针对kube proxy签发证书
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-proxy-csr.json | cfssljson -bare kube-proxy # 校验产生的证书 $ ls kube-proxy* kube-proxy.csr kube-proxy-csr.json kube-proxy-key.pem kube-proxy.pem
6. Scheduler 客户端证书
6.1 kube scheduler客户端证书签名请求
cat > kube-scheduler-csr.json <<EOF
{
"CN": "system:kube-scheduler",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "system:kube-scheduler",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
6.2 针对kube scheduler签发证书
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-scheduler-csr.json | cfssljson -bare kube-scheduler # 校验产生的证书 $ ls kube-scheduler* kube-scheduler.csr kube-scheduler-csr.json kube-scheduler-key.pem kube-scheduler.pem
7. Kuberenetes API证书
kube-api服务器证书主机名称应该包含如下: - 所有控制器的主机名称 - 所有控制器的IP - 负载均衡器的主机名称 - 负载均衡器的IP - Kubernetes的服务(kubernetes默认的服务名称和IP均是10.32.0.1) - localhost
CERT_HOSTNAME=10.32.0.1,<master node 1 Private IP>,<master node 1 hostname>,<master node 2 Private IP>,<master node 2 hostname>,<master node 3 Private IP>,<master node 3 hostname><API load balancer Private IP>,<API load balancer hostname>,127.0.0.1,localhost,kubernetes.default
$ CERT_HOSTNAME=10.32.0.1,c720111.xiodi.cn,192.168.20.111,c720112.xiodi.cn,192.168.20.112,c720113.xiodi.cn,192.168.20.113,c720116.xiodi.cn,192.168.20.116,127.0.0.1,localhost,kubernetes.default
7.1 创建证书签名请求
$ cat > kubernetes-csr.json <<EOF
{
"CN": "kubernetes",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "Kubernetes",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
7.2 产生kubernetes API证书
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -hostname=${CERT_HOSTNAME} -profile=kubernetes kubernetes-csr.json | cfssljson -bare kubernetes
7.3 查看证书
$ ls kubernetes* kubernetes.csr kubernetes-csr.json kubernetes-key.pem kubernetes.pem
8. 服务帐户密钥对
服务帐户密钥对常用来签署服务帐户的token. 关于服务帐户参考链接:https://kubernetes.io/docs/reference/access-authn-authz/service-accounts-admin/
8.1 配置服务帐户的证书签名请求
$ cat > service-account-csr.json <<EOF
{
"CN": "service-accounts",
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "Westeros",
"L": "The North",
"O": "Kubernetes",
"OU": "Kubernetes The Hard Way",
"ST": "Winterfell"
}
]
}
EOF
8.2 针对服务帐户签发证书
$ cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes service-account-csr.json | cfssljson -bare service-account # 查看针对服务帐户签发的证书 $ ls service-account* service-account.csr service-account-csr.json service-account-key.pem service-account.pem
9. 复制证书到各个节点
$ cat workers.txt
c720114.xiodi.cn 192.168.20.114 root
c720115.xiodi.cn 192.168.20.115 root
$ cat controllers.txt
c720111.xiodi.cn 192.168.20.111 root
c720112.xiodi.cn 192.168.20.112 root
c720113.xiodi.cn 192.168.20.113 root
# Minion
$ IFS=$‘\n‘
$ for line in `cat workers.txt`; do
instance=`echo $line | awk ‘{print $1}‘`
user=`echo $line | awk ‘{print $3}‘`
rsync -zvhe ssh ca.pem ${instance}-key.pem ${instance}.pem ${user}@${instance}:/root/
done
# Master
$ for instance in c720111.xiodi.cn c720112.xiodi.cn c720113.xiodi.cn; do
rsync -zvhe ssh ca.pem ca-key.pem kubernetes-key.pem kubernetes.pem service-account-key.pem service-account.pem root@${instance}:/root/
done
===4. 针对k8s各个组件创建kubeconfig===
kubeconfig常用来在kubernetes组件之间和用户到kubernetes之间。kubeconfig主要包含三件事情:
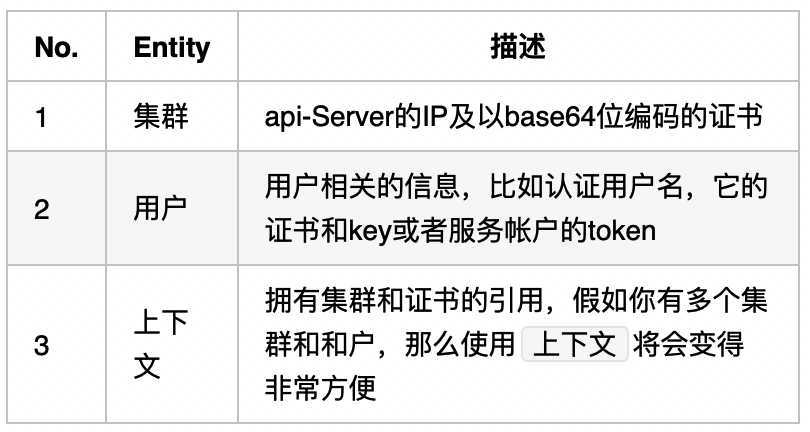
在本小节中,我们将会产生如下组件的kubeconfig:
1. kubelet kubeconfig
2. kube Proxy kubeconfig
3. Controller Manager kubeconfig
4. Kube Scheduler kubeconfig
5. admin用户的kubeconfig
4.1 产生kubelet的kubeconfig
在kubeconfig中的user应该是system:node:<Worker_name>,它应该匹配我们在产生kubelet client证书的主机名称。
$ cat haproxy.txt
c720116.xiodi.cn 192.168.20.116
$ chmod +x kubectl
$ cp kubectl /usr/local/bin/
$ KUBERNETES_PUBLIC_ADDRESS=`cat nginx_proxy.txt | awk ‘{print $2}‘`
$ IFS=$‘\n‘
$ for instance in c720114.xiodi.cn c720115.xiodi.cn; do
kubectl config set-cluster kubernetes-the-hard-way --certificate-authority=ca.pem --embed-certs=true --server=https://${KUBERNETES_PUBLIC_ADDRESS}:6443 --kubeconfig=${instance}.kubeconfig
kubectl config set-credentials system:node:${instance} --client-certificate=${instance}.pem --client-key=${instance}-key.pem --embed-certs=true --kubeconfig=${instance}.kubeconfig
kubectl config set-context default --cluster=kubernetes-the-hard-way --user=system:node:${instance} --kubeconfig=${instance}.kubeconfig
kubectl config use-context default --kubeconfig=${instance}.kubeconfig
done
$ ls
c720114.xiodi.cn.kubeconfig c720115.xiodi.cn.kubeconfig
4.2 产生kube-proxy kubeconfig
$ KUBERNETES_PUBLIC_ADDRESS=`cat nginx_proxy.txt | awk ‘{print $2}‘`
$ {
kubectl config set-cluster kubernetes-the-hard-way --certificate-authority=ca.pem --embed-certs=true --server=https://${KUBERNETES_PUBLIC_ADDRESS}:6443 --kubeconfig=kube-proxy.kubeconfig
kubectl config set-credentials system:kube-proxy --client-certificate=kube-proxy.pem --client-key=kube-proxy-key.pem --embed-certs=true --kubeconfig=kube-proxy.kubeconfig
kubectl config set-context default --cluster=kubernetes-the-hard-way --user=system:kube-proxy --kubeconfig=kube-proxy.kubeconfig
kubectl config use-context default --kubeconfig=kube-proxy.kubeconfig
}
$ ls kube-proxy.kubeconfig
kube-proxy.kubeconfig
原文:https://www.cnblogs.com/shanghai1918/p/12888117.html
