Linux的文件特殊权限
SetUID
1) SetUID 是什么
SetUID 的功能可以这样理解:
- 只有可以执行的二进制程序才能设定 SUID 权限
- 命令执行者要对该程序拥有 x(执行)权限
- 命令执行者在执行该程序时获得该程序文件属主的身份(在执行程序的过程中灵魂附体为文件的属主)
- SetUID 权限只在该程序执行过程中有效,也就是说身份改变只在程序执行过程中有效
[root@iZbp145axkc98giot5b448Z ~]# ll /etc/passwd -rw-r--r-- 1 root root 1066 Apr 7 21:56 /etc/passwd [root@iZbp145axkc98giot5b448Z ~]# ll /etc/shadow ---------- 1 root root 704 Apr 7 21:56 /etc/shadow
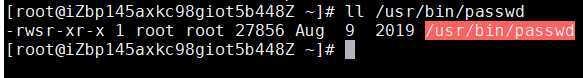
/usr/bin/passwd 命令拥有特殊权限 SetUID , 也就是在属主的权限位的执行权限上是 s。 可以这样来理解它: 当一个具有执行权限的文件设置 SetUID 权限后,用户执行这个文件时将以文件所有者的
身份执行。/usr/bin/passwd 命令具有 SetUID 权限,所有者为 root (Linux 中的命令默认所有者都是 root),也就是说当普通用户使用 passwd 更改自己密码的时候,那一瞬间突然灵魂附体了,实际是在用 passwd
命令所有者 root 的身份在执行 passwd 命令, root 当然可以将密码写入/etc/shadow 文件 ,所以普通用户也可以修改/etc/shadow 文件,命令执行完成后该身份也随之消失
如果取消 SetUID 权限,则普通用户就不能修改自己的密码了 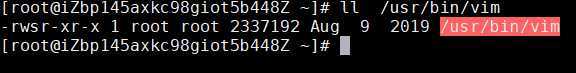
4) 有几点建议:
关键目录应严格控制写权限。比如“/”、“/usr”等;
用户的密码设置要严格遵守密码三原则;
对系统中默认应该具有 SetUID 权限的文件作一列表,定时检查有没有这之外的文件被设置了 SetUID 权限。
[root@iZbp145axkc98giot5b448Z ~]# find / -perm -4000 -o -perm -2000 /usr/libexec/dbus-1/dbus-daemon-launch-helper /usr/libexec/openssh/ssh-keysign /usr/libexec/utempter/utempter /usr/sbin/postdrop /usr/sbin/usernetctl /usr/sbin/netreport /usr/sbin/pam_timestamp_check /usr/sbin/postqueue /usr/sbin/unix_chkpwd /usr/bin/gpasswd /usr/bin/write /usr/bin/umount /usr/bin/chsh /usr/bin/at /usr/bin/crontab /usr/bin/mount /usr/bin/chage /usr/bin/sudo /usr/bin/wall /usr/bin/newgrp /usr/bin/passwd /usr/bin/su /usr/bin/vim /usr/bin/pkexec /usr/bin/chfn /usr/bin/ssh-agent /usr/lib/polkit-1/polkit-agent-helper-1 /var/log/journal
SetGID
1)针对文件的作用
SGID 即可以针对文件生效, 也可以针对目录生效,这和 SUID 明显不同。如果针对文件, SGID 的含义如下:
- 只有可执行的二进制程序才能设置 SGID 权限
- 命令执行者要对该程序拥有 x(执行)权限
- 命令执行在执行程序的时候,组身份升级为该程序文件的属组
- SetGID 权限同样只在该程序执行过程中有效,也就是说组身份改变只在程序执行过程中有效
[root@localhost ~]# ll /var/lib/mlocate/mlocate.db -rw-r----- 1 root slocate 1838850 1 月 20 04:29 /var/lib/mlocate/mlocate.db
发现属主权限是 rw,属组权限是 r,但是其他人权限是 0:
[root@localhost ~]# ll /usr/bin/locate -rwx--s--x 1 root slocate 35612 8 月 24 2010 /usr/bin/locate
当普通用户 user1 执行 locate 命令时,会发生如下事情:
- /usr/bin/locate 是可执行二进制程序,可以赋予 SGID
- 执行用户 user1 对/usr/bin/locate 命令拥有执行权限
- 执 行 /usr/bin/locate 命 令 时 , 组 身 份 会 升 级 为 slocate 组 , 而 slocate 组 对/var/lib/mlocate/mlocate.db 数据库拥有 r 权限,所以普通用户可以使用 locate 命令查询mlocate.db 数据库命令结束, user1 用户的组身份返回为 user1 组
2)针对目录的作用
如果 SGID 针对目录设置,含义如下:
- 普通用户必须对此目录拥有 r 和 x 权限,才能进入此目录
- 普通用户在此目录中的有效组会变成此目录的属组
- 若普通用户对此目录拥有 w 权限时,新建的文件的默认属组是这个目录的属组
这样写的实在太难看明白了,举个例子:
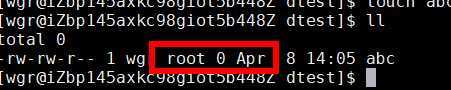
[root@iZbp145axkc98giot5b448Z tmp]# mkdir dtest [root@iZbp145axkc98giot5b448Z tmp]# ll total 6504 srwxr-xr-x 1 root root 0 Apr 7 22:12 Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7CBA)> drwxr-xr-x 3 root root 4096 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832 -rw-r--r-- 1 root root 6620890 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832.zip drwxr-xr-x 2 root root 4096 Apr 8 14:03 dtest drwx------ 3 elsearch elsearch 4096 Apr 7 22:32 elasticsearch.z6k2RXwo drwxr-xr-x 2 elsearch elsearch 4096 Apr 7 22:32 hsperfdata_elsearch drwxr-xr-x 2 root root 4096 Apr 7 22:31 hsperfdata_root drwx------ 3 root root 4096 Apr 7 22:12 systemd-private-47ba1a30f74443359eee1235e77c3628-chronyd.service-CPTRMh drwx------ 2 root root 4096 Apr 7 21:52 tmp.PhvlqNXdZM drwx------ 2 root root 4096 Apr 7 21:45 tmp.QaZeCT0j34 drwx------ 2 root root 4096 Apr 7 22:13 tmp.uD7vBpaEIG [root@iZbp145axkc98giot5b448Z tmp]# chmod g+s dtest [root@iZbp145axkc98giot5b448Z tmp]# ll total 6504 srwxr-xr-x 1 root root 0 Apr 7 22:12 Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7CBA)> drwxr-xr-x 3 root root 4096 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832 -rw-r--r-- 1 root root 6620890 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832.zip drwxr-sr-x 2 root root 4096 Apr 8 14:03 dtest drwx------ 3 elsearch elsearch 4096 Apr 7 22:32 elasticsearch.z6k2RXwo drwxr-xr-x 2 elsearch elsearch 4096 Apr 7 22:32 hsperfdata_elsearch drwxr-xr-x 2 root root 4096 Apr 7 22:31 hsperfdata_root drwx------ 3 root root 4096 Apr 7 22:12 systemd-private-47ba1a30f74443359eee1235e77c3628-chronyd.service-CPTRMh drwx------ 2 root root 4096 Apr 7 21:52 tmp.PhvlqNXdZM drwx------ 2 root root 4096 Apr 7 21:45 tmp.QaZeCT0j34 drwx------ 2 root root 4096 Apr 7 22:13 tmp.uD7vBpaEIG [root@iZbp145axkc98giot5b448Z tmp]# ll -d dtest/ drwxr-sr-x 2 root root 4096 Apr 8 14:03 dtest/ [root@iZbp145axkc98giot5b448Z tmp]# cd dtest/ [root@iZbp145axkc98giot5b448Z dtest]# ll total 0 [root@iZbp145axkc98giot5b448Z dtest]# cd .. [root@iZbp145axkc98giot5b448Z tmp]# chmod 777 dtest/ [root@iZbp145axkc98giot5b448Z tmp]# ll total 6504 srwxr-xr-x 1 root root 0 Apr 7 22:12 Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7CBA)> drwxr-xr-x 3 root root 4096 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832 -rw-r--r-- 1 root root 6620890 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832.zip drwxrwsrwx 2 root root 4096 Apr 8 14:03 dtest drwx------ 3 elsearch elsearch 4096 Apr 7 22:32 elasticsearch.z6k2RXwo drwxr-xr-x 2 elsearch elsearch 4096 Apr 7 22:32 hsperfdata_elsearch drwxr-xr-x 2 root root 4096 Apr 7 22:31 hsperfdata_root drwx------ 3 root root 4096 Apr 7 22:12 systemd-private-47ba1a30f74443359eee1235e77c3628-chronyd.service-CPTRMh drwx------ 2 root root 4096 Apr 7 21:52 tmp.PhvlqNXdZM drwx------ 2 root root 4096 Apr 7 21:45 tmp.QaZeCT0j34 drwx------ 2 root root 4096 Apr 7 22:13 tmp.uD7vBpaEIG [root@iZbp145axkc98giot5b448Z tmp]# useradd wgr [root@iZbp145axkc98giot5b448Z tmp]# su - wgr [wgr@iZbp145axkc98giot5b448Z ~]$ cd /tmp [wgr@iZbp145axkc98giot5b448Z tmp]$ ll total 6504 srwxr-xr-x 1 root root 0 Apr 7 22:12 Aegis-<Guid(5A2C30A2-A87D-490A-9281-6765EDAD7CBA)> drwxr-xr-x 3 root root 4096 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832 -rw-r--r-- 1 root root 6620890 Apr 7 21:38 aliyun_assist_cb6fdc57727f94b9206741570ae89832.zip drwxrwsrwx 2 root root 4096 Apr 8 14:03 dtest drwx------ 3 elsearch elsearch 4096 Apr 7 22:32 elasticsearch.z6k2RXwo drwxr-xr-x 2 elsearch elsearch 4096 Apr 7 22:32 hsperfdata_elsearch drwxr-xr-x 2 root root 4096 Apr 7 22:31 hsperfdata_root drwx------ 3 root root 4096 Apr 7 22:12 systemd-private-47ba1a30f74443359eee1235e77c3628-chronyd.service-CPTRMh drwx------ 2 root root 4096 Apr 7 21:52 tmp.PhvlqNXdZM drwx------ 2 root root 4096 Apr 7 21:45 tmp.QaZeCT0j34 drwx------ 2 root root 4096 Apr 7 22:13 tmp.uD7vBpaEIG [wgr@iZbp145axkc98giot5b448Z tmp]$ cd dtest [wgr@iZbp145axkc98giot5b448Z dtest]$ ll total 0 [wgr@iZbp145axkc98giot5b448Z dtest]$ touch abc [wgr@iZbp145axkc98giot5b448Z dtest]$ ll total 0 -rw-rw-r-- 1 wgr root 0 Apr 8 14:05 abc [wgr@iZbp145axkc98giot5b448Z dtest]$
Sticky BIT
Sticky BIT 粘着位,也简称为 SBIT。 SBIT 目前仅针对目录有效,它的作用如下:
- 粘着位目前只对目录有效
- 普通用户对该目录拥有 w 和 x 权限,即普通用户可以在此目录拥有写入权限
- 如果没有粘着位,因为普通用户拥有 w 权限,所以可以删除此目录下所有文件,包括其他用户建立的文件。一但赋予了粘着位,除了 root 可以删除所有文件,普通用户就算拥有 w 权限,也只能删除自己建立的文件,但是不能删除其他用户建立的文件。
[test1@iZbp145axkc98giot5b448Z test]$ ll total 0 -rw-r--r-- 1 root root 0 Apr 8 14:22 aaa -rw-r--r-- 1 root root 0 Apr 8 14:22 bbb -rw-rw-r-- 1 wgr wgr 0 Apr 8 14:24 ccc -rw-rw-r-- 1 wgr wgr 0 Apr 8 14:24 ddd -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 eee -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 fff [test1@iZbp145axkc98giot5b448Z test]$
[root@iZbp145axkc98giot5b448Z test]# rm -f ccc [root@iZbp145axkc98giot5b448Z test]# ll total 0 -rw-r--r-- 1 root root 0 Apr 8 14:22 aaa -rw-r--r-- 1 root root 0 Apr 8 14:22 bbb -rw-rw-r-- 1 wgr wgr 0 Apr 8 14:24 ddd -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 eee -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 fff [root@iZbp145axkc98giot5b448Z test]#
[wgr@iZbp145axkc98giot5b448Z test]$ touch ddd [wgr@iZbp145axkc98giot5b448Z test]$ ll total 0 -rw-r--r-- 1 root root 0 Apr 8 14:22 aaa -rw-r--r-- 1 root root 0 Apr 8 14:22 bbb -rw-rw-r-- 1 wgr wgr 0 Apr 8 14:24 ddd -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 eee -rw-rw-r-- 1 test1 test1 0 Apr 8 14:25 fff [wgr@iZbp145axkc98giot5b448Z test]$ rm -rf eee rm: cannot remove ‘eee’: Operation not permitted [wgr@iZbp145axkc98giot5b448Z test]$ touch qqq [wgr@iZbp145axkc98giot5b448Z test]$
以上所有操作均提示Operation not permitted,表明Sticky权限已发挥作用.普通用户在设定了Sticky位的目录下创建的子目录不会继承这个Sticky权限,所以要注意设定好自己目录的权限.
原文:https://www.cnblogs.com/dalianpai/p/12659780.html
